The term used to describe. The voluntary near-miss reporting system used for the rail industry in the United Kingdom is the.
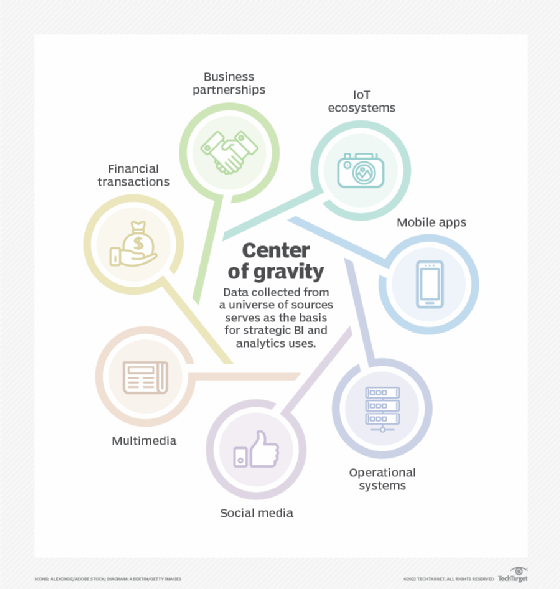
Data Collection Methods Challenges And Key Steps
Requirements determination involves studying the existing system and gathering details to find out what are the.

. Operations and Supply Chain Management 14th Edition Edit edition Solutions for Chapter 24 Problem 9OQ. Information worker Related Mcqs. A requirement is a vital feature of a new system which may include processing or capturing of data controlling the activities of business producing information and supporting the management.
The next time you visit the site the browser will easily. With SSI the power to control personal data resides with the individual. The analyst needs to fully understand the current system.
It covers the who what when where why and how of data entry processing storage information output and system controls. Fact-finding is an important activity in system investigation. Adapting the system to new requirements C.
All of the above. Discuss methods on how to hide information on victim systems that will. People respond to written statements.
Recovering the system D. The output from a transaction processing system is used as input to a management information system. Based on interviews with the user the analyst writes a brief description of hisher understanding of the problem and reviews it with both the groups.
Internal system user D. It does not necessarily mean a electonic device. Several generations of Wireless Local Area Network WLAN devices have been developed and standardized over the years.
Systems Planning and Investigation. Forensic investigation witness examination and background checks to collect relevant evidence. Aggregate compare and summarizes the results to produced reports that tactical managers use to monitor control and predict future performance.
An information system commonly refers to a basic computer system but may also describe a telephone switching or environmental controlling system. An information system is any tool that is used to communicate and share information. The first source includes system log files containing system logs within the operating system as well as an overview of some tools that can be used in order to effectively understand these logs.
A department that is willing to cooperate with any outside investigation shows organizational. The initial responding law enforcement officer s andor other public safety official s or service provider s arriving at the scene prior to the arrival of the investigator s in charge. For example a murderer who tries to create false evidence so that possibly someone else is suspected of the crime they committed.
Student review 100. SSI means the individual or organization manages the elements that make up their identity and controls access to those credentials digitally. I am looking for the more common and correct term used when someone tries to misdirect investigations on a crime that has been committed.
An ongoing activity of systems support is________________. The first responsibility of a system analyst is to prepare a written statement of the objectives of the problem. File systems are also discussed including the effectiveness of metadata and their overall relevance to an investigation or analysis.
What term is used to refer to an individual who conducts investigations including forensic examinations on behalf of private citizens or businesses. This paper provides an overview of the role computer software plays within police forces with particular attention paid to crime analysis and investigation computer systems. The IS involves resources for shared or processed information as well as the people who manage the system.
Objects or materials that have retained the characteristics of other objects that have been physically pressed against them. In this stage the functioning of the system is to be understood by the system analyst to design the proposed system. ANSI 1 A person device program or computer system that uses an information system for the purpose of data processing in information exchange.
Various methods are used for this and these are known as fact-finding techniques. Describe what tools are used in forensic investigations to review what occurred on a targeted system or device. CODIS is the acronym for the Combined DNA Index System and is the generic term used to describe the FBIs program of support for criminal justice.
Self-sovereign identity SSI brings the same freedoms and personal autonomy to the internet in a safe and trustworthy system of identity management. Systems Investigation Problems and opportunities are identified Systems Analysis Existing systems and work processes are studied Systems Design Defines how the information system will do what it must do to solve the problem. The MIS system analyzes the input with routine algorithms ie.
Small sets of data that a web site will leave to be stored in your web browser when you visit a website. Implementation System components are assembled and the new or modified system is placed into operation. A specific identifier that represents a specific individual corporation public agency or school for example.
For example internet telephone fax machine writing pager. What term is used to describe actions by an individual that are performed in a way that could result in an injury. The narratives flowcharts diagrams and other written materials that explain how a system works.
What is the term used to describe arrangements to move clinical information across various information systems while still maintaining the meaning of the information being exchanged. People are considered part of the system because without them systems would not operate. A form used to record data about a transaction is an.

Covid 19 Oie World Organisation For Animal Health

Chapter 4 The Process Of Investigation Introduction To Criminal Investigation Processes Practices And Thinking

0 Comments